The financial sector is a favorite target for cybercriminals across the globe. And here at EastNets, we keep you up to date with hacking events that impact the world of finance. One of the largest and most shocking fraud events was the attack on the SWIFT network back in 2016; this resulted in an $81 million fraud attack impacting Bangladesh Bank. Worryingly, Research by EastNets found that attacks that focus on the SWIFT network are not uncommon, with 80% of banks surveyed experiencing at least one SWIFT fraud attempt since 2016.
As a response to the increasing fraud attacks against the SWIFT network and the payments systems in general, SWIFT created the Customer Security Control Framework (CSCF), which is part of their Customer Security Programme (CSP). This security framework describes mandatory and advisory security controls for any financial organization that utilizes its services.
In 2021, the CSCF was updated to v.2022.
The top 5 things a FI needs to know about SWIFT CSCF v.2022;
The current version SWIFT CSCF v.2021, published in July 2020, is due for attestation by the end of this year. However, hot on its heels is CSCF v.2022, published in July 2021, and organizations will need to attest compliance by December 2022.
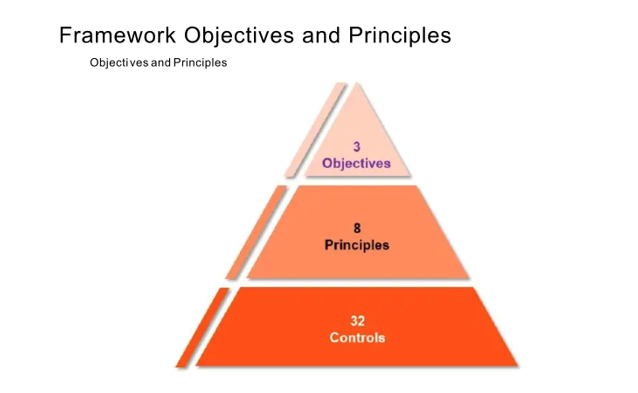
The structure of the CSCF is a three-tiered pyramid, comprising three overarching elements:
- Secure your Environment
- Know and Limit Access
- Detect and Respond
Source: SWIFT
SWIFT updates the CSCF on a regular basis to accommodate changes in the threat landscape. However, SWIFT attempts to limit changes to ensure that the industry has time to respond. To help with new compliance requirements, SWIFT also provides a change management system that ensures the industry has up to 18-months to respond to CSCF changes. To optimize v.2022 and future versions, SWIFT has created the CSCF Working Group made up of 23 National Members and User Groups to provide feedback on the framework.
The latest version of CSCF, v.2022, has several changes that need to be considered by an FI. Here are the top five things an FI needs to know to get into compliance with CSCF V.2022 are:
New advisory control 1.5A Customer Environment Protection;
This is a new advisory that details the requirements needed to secure the Customer Connector; this is analogous to the Secure Zone, a segmented and controlled environment tied to the SWIFT CSP control framework. SWIFT defines “Connectors” as “local software designed to facilitate communication with an external messaging interface or a communication interface (or both), or to a service provider (handling as such the external connection).” These types of interfaces can often be the target of a cyber-attack as they provide a point of access.
This new advisory is relevant for the A4 architecture type but also applies to the other three architecture types (A1, A2, and A3). Worth noting is that A4 architecture was introduced in CSCF v.2021 to cover customers with a non-SWIFT footprint to support new technology such as cloud and APIs. Note that the ‘Secure Zones’ are now clarified in v.2022 to support this update.
2.9 Transaction Business Controls is now mandatory;
SWIFT added 2.9 Transaction Business Controls, to CSCF v.2021 as an advisory control only. However, from CSCF v.2022, this control is now mandatory. This reflects the serious nature of the increasing threat of payment fraud. This mandate will apply to all architecture types and will significantly reduce fraudulent payments. To achieve this, CSCF v.2022 specifies that all financial institutions must restrict and monitor the data flows in payment transactions. Also worth noting is that control 2.9 aligns with the Committee of Payments and Market Infrastructures (CPMI) strategy to prevent payment fraud.
Limiting traffic outside of business hours Is one of the core requirements of this now mandatory control. Some of the sub-controls include the ability to issue and check confirmation messages as well as reconcile accounting records with end-of-day statement messages. Eastnets PaymentGuard is an AI-driven, multi-channel solution that is designed to manage these types of granular audit and process checks.
Scope extension to 1.2 Operating System Privileged Account Control;
Security hygiene opens vulnerabilities in a system and allows cybercriminals to exploit processes. To help mitigate security hygiene-related issues, CSCF control 1.2 (Operating System Privileged Account Control) has been extended in v.2022. This extension ensures that control 1.2 now covers basic security hygiene on end-user devices, and extends the scope to include general-purpose operator PCs as well as including architecture B. This control remains advisory rather than mandatory, however, this should be viewed as a best practice to mitigate payment fraud.
Independent assessment;
Previously, self-assessment in readiness for attestation of compliance with CSCF was allowed. However, from 2021 the CSCF assessment must now be performed by an independent assessor. This mandatory condition is carried out by “Community Standard Assessment” as part of the Independent Assessment Framework (IAF), which SWIFT requires to improve the accuracy of an attestation. This new mandate requires attestations to be assessed through either an internal or/and an external assessment.
Minor changes to keep a watchful eye over;
Last, but not least, several minor changes have been included in v.2022. Minor changes are important to be watchful of, as often minor changes become major control shifts, as the threat landscape changes and SWIFT community members make change requests.
Amongst the many minor changes to be aware of are:
- Control 2.7: network devices are now in scope under this control
- Control 4.2: timed One-Time Passwords (TOTP) and soft tokens are now added as Multi-Factor Authentication (MFA) options
- Control 5.1: ensure accountability and traceability of (re)assigned and delegated
- accounts; explicitly refer to network devices
- Control 5.2: explicitly refer to non-connected tokens
- Control 6.4: provide guidance on global log retention to support forensics in line with
local legislation - Control 7.2: split ‘annual security awareness’ expectation from ‘maintaining knowledge over time
It is important that a financial institution recognizes that the SWIFT CSCF is updated annually. This change, however, builds on previous versions, so you can continue to use attestation with a previous version of the CSCF as a compliance starting point to meet the new version requirements.
Organizations must attest to CSCF v2022 between July 2022 and December
-
To ensure your hard work is compliant and in readiness for attestation, an FI should begin this work now.
SWIFT will run dedicated seminars in early 2022 to help your company with attestation of compliance for CSCF v.2022.
Download Eastnet’s factsheet addressing the new control 2.9 and further information on how PaymentsGuard can help your FI meet the new CSCF v.2022 regulation.





